"There are two types of companies," said former Cisco CEO John Chambers in a 2015 World Economic Forum speech. "Those who have been hacked, and those who don’t yet know they have been hacked."
This quote exemplifies a stark reality: Cybercrime is easier than ever to perpetrate, thanks to the internet and the proliferation of computing devices, which are called endpoints by Information Technology (IT) professionals. Criminals can find kits containing pre-built malware for as little as a few dollars online.
Malware, a portmanteau word combining malicious and software, is a general term describing a slew of digital tactics employed by criminal hackers to intentionally cause harm. Organizations with inadequate IT security are particularly vulnerable, and these tend to be small businesses.
Cyberattacks have also grown in sophistication and complexity. The days of simply relying on your computer’s built-in antivirus software are over. Businesses need the best endpoint security software to remain protected.
To understand the damage malware can inflict, take a look at this bestiary of common malware attack types. You can see the security challenges your business is up against in order to prevent cyberattacks.
The 10 types of malware (and how to spot them, below):
- Virus
- Worms
- Trojans
- Polymorphic malware
- Ransomware
- Rootkits
- Keyloggers
- Bots
- Spyware and adware
- Mobile malware
1. Viruses
The term malware is often used interchangeably with computer viruses, but they’re not identical. Viruses are a subclass of malware. They’ve been around so long that the term became synonymous with malware in general.
A virus modifies computer files by inserting its code into another program. Security experts call the host file "infected" when this happens. The virus remains dormant until a user or computer process accesses the infected file. Then the virus executes, doing its damage.
A malware virus self-replicates just like a biological virus. Once activated, the virus spreads to other files and programs across your computer.
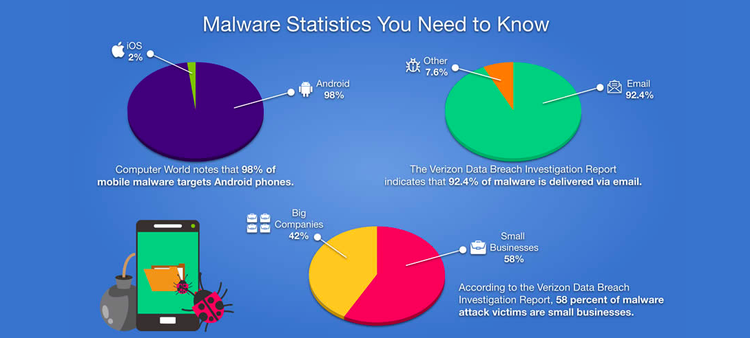
Viruses and other malware target the most susceptible prey. Image source: Author
Antivirus programs usually quarantine or delete infected files. However, it’s difficult to actually cleanse the file of the virus because the virus code is so intertwined with the software that it’s infected.
Viruses are not as commonly used today. The internet allows cyberattacks to spread more efficiently than a computer virus.
2. Worms
A worm and a virus are similar in that they propagate copies of themselves, but, unlike viruses, worms don’t require the infected program to execute in order to activate. Worms exploit software vulnerabilities or use techniques designed to trick people into introducing it into your IT network such as enticing users to click on an emailed file containing the worm.
Because worms run independently of any infected host files, they can spread across computer networks within minutes. Once in place, worms perform harmful activities such as deleting files and stealing sensitive data. Worms are so effective that governments use them for cyberespionage.
As worms self-replicate, they take up hard drive space and slow down your computer. If you notice your computer’s free space or performance is declining, or that files are disappearing, these are signs your system has been infected with a worm.
3. Trojans
Appropriately named after the Iliad’s famed Trojan Horse, the malware called Trojans disguises itself as desirable software and tricks users into downloading it. Trojans impersonate free games, useful apps, important email attachments, and even antivirus software.
Trojans are the advance guard of a malicious hacker. Once downloaded, Trojans open doors to give cybercriminals access to your system. They don’t self-replicate, relying instead on unwitting users to spread the malware.
Trojans work in conjunction with other malware types to execute the attacker’s goals. Signs of a Trojan infection include the machine starting to perform slowly, suddenly increasing its internet use, and unexpectedly freezing or crashing repeatedly.
4. Polymorphic malware
Polymorphic malware is a particularly sophisticated class of malware. It avoids attempts by antivirus to stop it by constantly changing its identifiable features.
With each file it infects, polymorphic malware adjusts parts of itself to make it difficult to detect. Some strive to limit the mutation rate over time to make antivirus scans unreliable in discovering the full extent of the infection.
A dependable detection method is to use pattern analysis to identify the characteristics of polymorphic malware in action. Advanced security techniques, such as threat hunting and endpoint detection and response (EDR), can find difficult-to-locate infections, including polymorphic malware.
5. Ransomware
One of the most damaging forms of malware forms is ransomware. The name says it all. A cybercriminal launches an attack that seeks to encrypt your files and data, blocking your access to it.
The hacker then demands a ransom in return for releasing the data. Even if you pay the ransom, you may not get the data back.
You can identify a ransomware attack when unauthorized file encryption starts taking place. Regularly backing up your files to a safe storage location can help you recover from a ransomware attack.
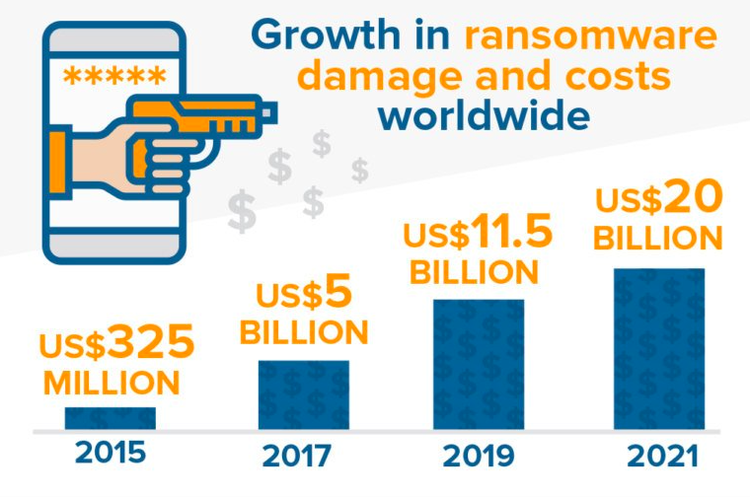
The rapid growth in ransomware damage attests to its popularity among criminals. Image source: Author
Combine regular backups with endpoint security software designed to look for unauthorized encryption attempts. This protection can also automatically roll back the ransomware changes, effectively stopping the attack and recovering your data.
6. Rootkits
Cybercriminals use rootkits to take control of your computer. Rootkits are software giving criminals remote control over your device with full administrative privileges to make any changes such as removing your antivirus software.
Because this attack type has control over your computer, your endpoint protection is often blocked from doing its job. An indicator of a potential rootkit infection is when you see malware repeatedly returning despite your antivirus cleaning up infected files.
Rootkits perform computer actions as a human would. They are commonly employed for ad fraud. A rootkit can open invisible browsers and click on ads to generate income for the attacker.
7. Keyloggers
As its name implies, keyloggers monitor your keystrokes and other computer activity to steal passwords and other confidential information. Keyloggers are legal programs used by companies to monitor employees. It’s only when they’re combined with malicious objectives that keyloggers become a threat.
Keyloggers don’t need to slip onto your computer to steal your information. A common tactic is for the criminal to send an email that looks like it’s from your bank with a link to a fake login page. In this way, the criminal tricks you into typing your credentials on the fake page, and the keyloggers record every keystroke, including when you pressed the shift key to capitalize letters.
Antivirus software can catch keyloggers on your computer. If your company uses keyloggers for legitimate purposes, those will require whitelisting to make sure your antivirus stops the malicious computer program and not yours.
8. Bots
Bots in themselves are not malicious. They are software applications widely used for legitimate purposes. They perform automated tasks involving repetitive actions such as crawling webpages to index content into search engines.
Cybercriminals use bot technology to enslave your computers to do their bidding. Doing so allows criminals to obtain the magnitude of computing power needed for large-scale, coordinated attacks.
Using the internet, criminals connect your devices to thousands of others outside those depicted in your IT network diagram. Security professionals call machines combined in this way a botnet.
Criminals use botnets to commit a range of malicious actions.
- DDoS: Bots can flood a website with traffic, bringing the site down in what’s known as a distributed denial-of-service (DDoS) attack.
- Advertising click fraud: Bots repeatedly click on ads to generate revenue for criminals.
- Spambots: Bots collect email addresses from online sources and send email spam.

Cyberattacks happen more frequently than we like to think. Image source: Author
9. Spyware and adware
Spyware, as its name indicates, is malware used to spy on your computer activity. Governments employ spyware for espionage.
Malicious actors use spyware to keep tabs on people they know or in surgical attacks against celebrities, government officials, and business people. It’s used for financial gain or to steal proprietary information.
Various degrees of spyware are in widespread use. A subclass called adware exists for legally permissible purposes such as ad targeting where a company tracks your interests to deliver ads targeted toward those affinities.
Some companies require adware acceptance as part of their service agreements. This led to the European Union’s passage of the General Data Protection Regulation (GDPR) law to protect user privacy and security.
Spyware ventures into the malware realm when it’s installed without your knowledge and consent. It uses Trojans to trick people into downloading it, or it exploits software vulnerabilities to bypass security defenses. The infamous DarkHotel spyware used hotel wifi networks to distribute it.
Spyware attempts to remain on your computer as long as possible in what security experts call an advanced persistent threat (APT). It acts in conjunction with other malware, such as keyloggers, for theft purposes.
Endpoint protection software can catch spyware and adware. The more sophisticated APTs may require threat hunting and EDR techniques to identify and stop them.
10. Mobile malware
Malware can infect mobile devices just like any other computer. Smartphones are particularly irresistible targets for cybercriminals given the treasure trove of personal data on these devices.
Mobile malware works similarly to the other malware types on this list, but it poses a greater threat for several reasons.
- Apps: We frequently add new apps to our mobile phones. Apps often ask for access to your geolocation, camera, and microphone. Once we grant permission, an app carrying malicious code can now easily spy on us, silently collecting information.
- Bluetooth: Malware can infect your device through its Bluetooth, particularly if you’re using older versions of Google’s Android operating system.
- Jailbreaking: If you jailbreak an Apple device, called rooting when referring to Android devices, you lose the security protections that came from the manufacturer.
Android-powered devices are more often targeted by cybercriminals due to Android’s larger user base compared to Apple. Signs of an infection include a sudden decline in your phone’s battery life, your contacts receiving text messages you didn’t send asking them to click a link, and mysterious increases in data usage.
Final advice about malware
Cybercriminals continuously evolve their attacks to evade detection and improve their ability to infect devices. For instance, malware traditionally infected computer files but is increasingly moving to a fileless malware approach that leaves no obvious trace. This makes it difficult to detect and remove even if your organization has a security operations center (SOC).
To keep pace, adopt endpoint security software such as Bitdefender GravityZone. Endpoint protection is a must for any business. These software platforms not only include antivirus and other protection layers designed to stop the malware threats on this list, but they also highlight IT network vulnerabilities to proactively strengthen your security.
Complement this with endpoint detection and response capabilities to catch threats that slip through your defenses. EDR, alongside endpoint protection software, delivers a holistic security solution and keeps the various types of malware at bay.
Our Small Business Expert
We're firm believers in the Golden Rule, which is why editorial opinions are ours alone and have not been previously reviewed, approved, or endorsed by included advertisers. The Ascent does not cover all offers on the market. Editorial content from The Ascent is separate from The Motley Fool editorial content and is created by a different analyst team.