A Small Business Guide to IT Risk Management
Your information technology (IT) department oversees a technical landscape becoming more complex and more vulnerable to threats every day. This requires you answer questions such as, "Which threats have the highest priority for my business?" and "What's my risk tolerance?"
IT risk management formalizes risk assessment and subsequent mitigation efforts. You can't eliminate risk, but we'll go over risk management strategies to minimize its impact on your small business.
Overview: What is IT risk management?
IT risk management oversees, measures, controls, and reports on risk-related issues within the IT department. Successful risk management provides high-quality data availability, confidentiality, and integrity for internal and external stakeholders.
The classic model to calculate risk has three variables:
- Threat: A defined hazard such as a dedicated denial-of-service (DDoS) attack or phishing attempts
- Vulnerability: An identified gap within your security system
- Consequence: Amount of harm the company suffers due to the threat
Once these variables are defined -- for example, you can rate each one on a scale of 1-10 based on level of severity -- risk is calculated as:
Risk = Threat x Vulnerability x Consequence
Every organization faces multiple constant data security threats, but all threats are not created equal. Prioritize threats based on their potential impacts on business operations and stakeholder confidence.
Your basic risk management plan consists of four steps: identify, assess, control the risk, and then review those controls.
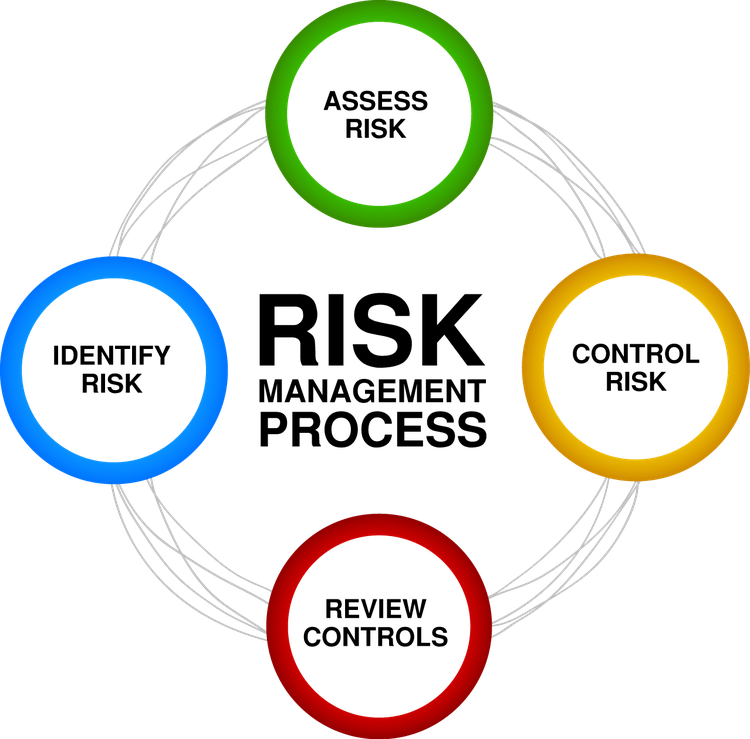
Risk management is an ongoing, recursive process. Image source: Author
The IT risk management process typically incorporates a dedicated information security management system (ISMS) and Information Technology Infrastructure Library (ITIL) Version 3 (v3) protocols.
ITIL processes enhance the overall IT service life cycle and better integrate IT department activities with business objectives and procedures.
Managed service providers (MSPs), which supply IT services to external customers or businesses with extended enterprise networks, may employ a security operations center (SOC).
The SOC concentrates solely on network security and leaves general network performance and direct end-user support to a network operations center (NOC) or IT help desk.
What does IT risk management look like in practice
IT risk management is similar to driving your car down the highway as different things hit your windshield. You can't avoid bugs, gravel, or rain -- or IT risks.
When you're driving, you engage in risk mitigation. You accept bugs hitting your windshield because the potential damage is negligible. If you're driving behind a gravel truck, you might pass it when you have the chance to avoid any rocks that might fly out of it.
If that's impossible, you could let another vehicle get ahead of you to transfer some risk to it. Or, if you find yourself in a raging downpour, you can slow down to reduce the risk from limited visibility or hydroplaning on the road.
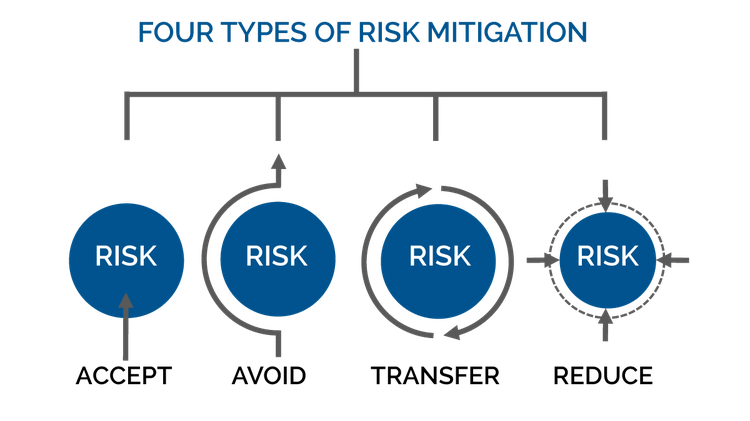
Risk mitigation strategies recognize that you cannot eliminate risk. Image source: Author
IT risk assessment is critical to determine your risk tolerance and strategies. Categorize identified risks and determine which ones you can accept, avoid, transfer, or reduce.
1. Quantitative risk assessment
Quantitative assessment takes the risk assessment model one step further by calculating the potential financial impact for each threat scenario. The bottom-line cost of threats and their remediation is a useful starting point to determine optimal risk mitigation.
- Financial risk: For each risk scenario, calculate the potential financial costs for hardware, software, and devices based on their risk exposure.
- Mitigation cost: Calculate the cost for each mitigation type; ones that cost more than the projected financial risk can be discarded. Then, choose the remaining mitigation option that provides the best return on investment (ROI).
A quantitative analysis uses hard data to inform your risk strategies, but its focus on financial costs does not account for the other important factors a qualitative analysis includes.
2. Qualitative risk assessment
Instead of using hard data, a qualitative assessment answers questions such as, “How would service levels be impacted?” and "What would be the impact on our reputation?" This approach is subjective because it uses responses and perspectives from multiple stakeholders to generate its results.
- Business impact: This assessment identifies the risks with the greatest potential impact on overall business processes. It looks for the cascading effects an unaddressed risk can have throughout your company and how it could affect the productivity of multiple workgroups and departments.
- Reputation impact: Qualitative risk assessment evaluates the potential external impact on end users and customers, including customer satisfaction (CSAT) scores, customer churn rates, and social media interactions.
The inherent nature of a qualitative assessment is more amorphous than its quantitative counterpart. Perception is reality, though, and how your internal and external users perceive your IT capabilities directly affects your bottom line.
3. Problem management
Risk control is connected to your problem management processes. While incident management is inherently reactive -- IT personnel respond to low-level, unexpected events or user-submitted help tickets -- problem management is proactive.
- Recurring incidents: Problem management identifies the underlying cause of recurring events to formulate a mitigation risk strategy.
- Knowledge base: Both incident and problem management require a knowledge base, a central repository of approved information and processes for IT staff. Online knowledge base articles document how to mitigate different types of risk and can be easily updated to reflect recent events and incidents.
The best IT management software automates and streamlines problem and change management.
4. Emergency change management
Change management, another ITIL process, contributes to risk management. While routine and standard changes present little risk, emergency changes, which are approved by the emergency change advisory board (ECAB), quickly reduce risk during unexpected critical events or disasters.
- ECAB: This board requires representatives from IT areas, the rest of the business (such as financial services, HR, and marketing), and third-party vendors. The wide range of participants provides a cross-functional perspective of risk and threat evaluation.
- Emergency changes: While emergency changes -- a critical hotfix or response to a zero day exploit -- are expedited to reduce risk, using a defined emergency change process is critical. An ad hoc solution with no oversight or discussion beforehand can create more issues than it solves.
Your change management plans help you avoid needless service interruptions, unwanted expenses, and decreased CSAT scores.
5. Track your results
Tracking risk mitigation outcomes can be tricky because it's hard to calculate an absolute value for something that didn't happen or was minimized.
Comparative financial statistics -- year over year, quarter over quarter, or other defined time periods -- provide actionable insights about the results of your efforts.
- Downtime: Depending on the size of your company and industry, network downtime costs range from $137/minute to $9,000/minute. These costs include reduced employee productivity, lost e-commerce transactions, service-level agreement (SLA) financial penalties, and government fines for regulatory violations.
- Data loss: The costs of data loss from hacks, which may take weeks or months to detect, can be even more expensive than downtime. Direct costs include notification processes after a data breach, impact on sales revenue, and fines. Indirect costs include loss of customer confidence and lost deal opportunities. Hidden costs include lost employee productivity as you deal with the breach.
More granular performance metrics include number of identified threats versus realized threats, number and frequency of unanticipated threats, and threat mean time to resolution (MTTR).
Tips for successful IT risk management
These nuts-and-bolts tips will aid your efforts as you implement risk management strategies at your business.
1. Collaborate and communicate
The consequences of unaddressed risk reverberate throughout your entire business, which means risk management is too important to delegate to one person or department.
Effective risk management is holistic, incorporates multiple perspectives, and requires ongoing communication between stakeholders during initial assessment and subsequent mitigation.
2. Consider multiple scenarios
Multiple viewpoints help you avoid groupthink, locking into a single assessment or solution without adequate consideration of alternative possibilities. Even if one response to a threat seems "obvious," solicit additional suggestions and ideas to expand the scope of your assessment.
3. Use a risk register
A risk register identifies a half-dozen most probable current threats and the actions to take if they occur. To paraphrase Donald Rumsfeld, the former U.S. secretary of defense, the risk register lists:
- Known knowns: Things you know about the risk.
- Known unknowns: Things you know about the risk but could forget.
- Unknown unknowns: Things that exist regarding the risk that you don't know about.
- Positive risks: Opportunities related to the risk.
The risk register is a handy document that allows you to hit the ground running when an anticipated threat appears instead of having to start from scratch.
Manage risk or be a victim of it
You can't eliminate the risks your company's network and related IT assets face, but don't be their captive. A proactive risk management strategy, with input from multiple stakeholders, mitigates potential threats to your business and its external relationships.
Alert: our top-rated cash back card now has 0% intro APR until 2025
This credit card is not just good – it’s so exceptional that our experts use it personally. It features a lengthy 0% intro APR period, a cash back rate of up to 5%, and all somehow for no annual fee! Click here to read our full review for free and apply in just 2 minutes.
Our Research Expert
We're firm believers in the Golden Rule, which is why editorial opinions are ours alone and have not been previously reviewed, approved, or endorsed by included advertisers. The Ascent does not cover all offers on the market. Editorial content from The Ascent is separate from The Motley Fool editorial content and is created by a different analyst team.
Related Articles
View All Articles