Maybe you're like me and have a closet shelf at your office where your misfit hardware and software live.
The accumulated items on mine include several old laptops, 12-year-old QuickBooks installation CDs, things I don't even recognize -- a router? Maybe a modem an IT tech accidentally left behind? -- and a rat's nest of power adapter cords and connectors.
Multiply my shelf by a hundred, and that's the situation facing many information technology (IT) departments.
Your initially simple network and small collection of hardware and software mushrooms over time: a server added here, and software added there, plus printers, scanners, and computers that show up one day, get passed around from one person or department to another, and eventually die.
You can't afford an IT landscape that's a no-man's land without signposts indicating where anything is or how to get from one point to another.
Configuration management creates a comprehensive map of your IT environment, so we'll go over its principles, benefits, and the steps to incorporate it at your small business.
Overview: What is configuration management?
Configuration management (CM) identifies, verifies, and maintains information about IT assets -- servers, software, and digital devices -- within your enterprise network.
CM systems are typically part of IT management software, and once your network is complex enough, a dedicated configuration manager should oversee these assets.
Each asset, which is called a configuration item (CI), has three attributes:
- Technical: Information such as model number, software version, and manufacturer and hardware specifications, including data storage limits and networking speeds
- Ownership: Information such as purchase date, warranty, location, and person responsible
- Relationships: The connections between specific users (e.g., a human resources manager), hardware assets (e.g., a desktop computer), and applications (e.g., recruitment management software)
CI data is stored in a configuration management database (CMDB). The CMDB provides a complete picture of your IT environment instead of accessing this information piecemeal.
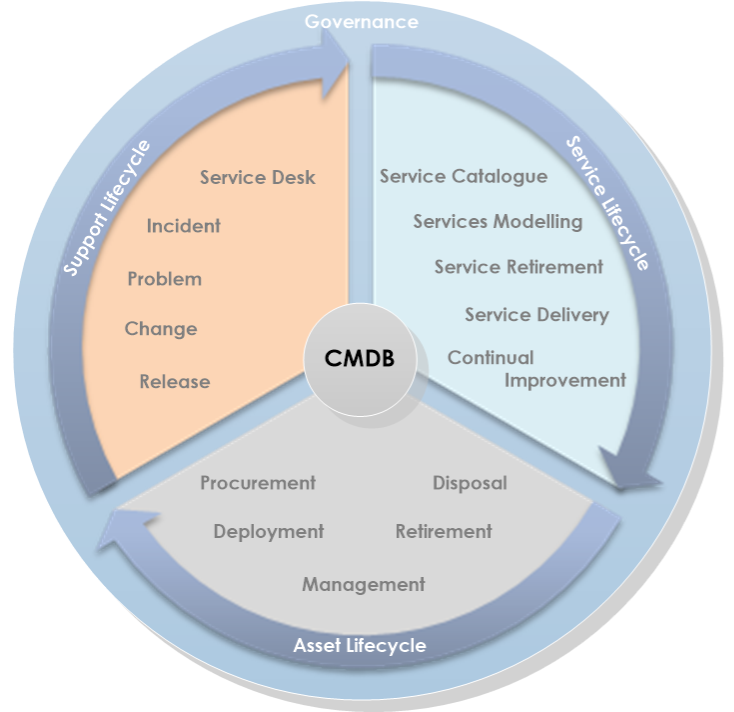
The CMDB incorporates a wide range of IT department activities and CI information. Image source: Author
The configuration management process is part of the Information Technology Infrastructure Library (ITIL) framework. ITIL processes and best practices work to better integrate IT activities with overall business objectives and procedures.
A CMDB also aids these ITIL processes:
If you want to align your IT department with ITIL principles, research IT help and service desk software. Some applications handle both day-to-day tasks like service requests and the bigger ITIL operational picture.
Benefits of configuration management
IT configuration management allows your IT team to centrally manage CIs for greater efficiency during daily operations and unexpected critical events.
1. Lower costs
Configuration management prevents unnecessary hardware and software duplication.
Better control over your network and data helps you avoid fines due to noncompliance with regulations such as the Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI DSS), and Sarbanes-Oxley Act.
2. Increased uptime
Every minute of website or network downtime costs you hundreds or even thousands of dollars. Configuration management's ongoing system maintenance and record keeping reduces downtime. Fewer recurring issues such as unauthorized software installs also make your network more stable.
3. Disaster recovery
Configuration management is integral to IT risk management. Whether you have a flooded data center, a dedicated denial-of-service (DDOS) attack, or have to roll back a bad deployment, this data helps get you back online more quickly.
How to get started with configuration management
ITIL configuration management is a complex undertaking requiring a significant investment of time, personnel, money, and resources. Follow these steps for the best return on investment (ROI).
Step 1: Develop a configuration management plan (CMP)
A configuration management plan (CMP) must address your current IT environment and be scalable as your small business and network footprint grows. A CMP contains multiple elements, but address these two infrastructure areas first:
- Governance: A Service Asset and Configuration Management (SACM) policy identifies the responsibilities of the configuration owner, configuration manager, CMDB administrator(s) and developers, and CI owners.
- Procedures: Define IT personnel interactions with the CMDB, how to document relationships between CIs, and the internal rules to organize information.
Once governance and basic procedures are documented, address CMP components such as scope, naming conventions, baselines, and verification and audit processes.

The CMP's six components provide a holistic overview of your IT network activities. Image source: Author
Take time to formulate your CMP and have multiple stakeholders provide input and review, because configuration management implementation requires a solid foundation and buy-in.
Step 2: Inventory your configuration items (CIs)
Conduct a complete inventory of your IT CIs. This inventory is more than a list of your hardware and software. It creates an overview of your IT infrastructure and its interrelationships.
CI and related information includes:
- Hardware
- Software
- Networks
- Databases
- Services
- Personnel
- Locations
- Technical and procedural documentation
This inventory is not a one-and-done activity. It's an ongoing process requiring IT management software that automatically detects new devices, software installs, and users.
Step 3: Identify CMDB data and sources
Your CMDB uses multiple sources to aggregate different data. Cataloging this information ensures a complete picture of your IT environment:
- Types of records: Includes ITIL management records, infrastructure and application records, knowledge management and known error records, service-level agreements (SLAs), operational-level agreements (OLAs), manufacturer specifications, and relevant company departments' and personnel information.
- Metadata: Identify data source, accuracy, purpose, level of detail, owner, users, and how the data is supported and maintained.
Consistent nomenclature and version control is critical for accurate record-keeping. Correctly identified documentation and data -- especially during disaster recovery -- saves time and prevents backtracking due to using outdated information.
Step 4: Audit your CMDB and CIs
"Garbage in, garbage out" (GIGO) is a computer science maxim because data output is only as good as the information used. Even small errors can multiply or become more significant over time, so initial data accuracy is essential:
- Internal audits: Checks performed by the CMP implementation team.
- External audits: Final checks performed outside the implementation team by other company personnel or third-party evaluators.
After the CMDB is complete, incorporate these audit processes with your continuous improvement strategy.
Step 5: Implement continuous improvement
Your CMDB is not static; it requires ongoing evaluation to improve its processes such as incident, problem, change, and release management.
Continuous improvement processes include:
- ITIL Continual Service Improvement (CSI): ITIL CSI uses a seven-step process to collect and assess data to formulate and evaluate improvement plans.
- Plan-do-check-act (PDCA): Unlike ITIL CSI, which is specific to IT departments, multiple industries use PDCA for continuous improvement.
Continuous improvement processes result in two types of changes: incremental and breakthrough.
Incremental changes are small tweaks that streamline a policy or procedure.
Breakthrough changes are larger in scope and require team consensus before implementation because they may fundamentally change the way a process is performed or the software applications used.
Map your IT environment today
You can't afford to be a stranger in a strange IT land of your own making. Implement a CMP with the best configuration management tools to increase uptime, lower costs, and recover more quickly after unexpected IT events.
Our Small Business Expert
We're firm believers in the Golden Rule, which is why editorial opinions are ours alone and have not been previously reviewed, approved, or endorsed by included advertisers. The Ascent does not cover all offers on the market. Editorial content from The Ascent is separate from The Motley Fool editorial content and is created by a different analyst team.