Every business requires endpoint security software to protect computers and other IT assets from cyberattacks. Small businesses are particularly vulnerable as cybercriminals assume SMBs are easy targets. The best endpoint security software stops cybercriminals from stealing your data and wreaking havoc on IT systems. Find peace of mind with these endpoint security solutions.
Securing your business against cyber threats is a must, but it's easier said than done. According to Small Business Administration research, a whopping 88% of small business owners feel their company is vulnerable to cyberattacks.
Two factors compound the challenge: (1) the explosion in device use as mobile phones and tablets increase in importance as business tools, and (2) the rapid growth in remote workers. These two factors combine to make it more difficult than ever to manage IT security.
So how can a business address this need? The answer is endpoint security software. This software protects your computers, servers, and mobile devices -- collectively referred to as endpoints -- from cyberattacks.
The endpoint security products on this list offer different capabilities to meet diverse business requirements. Some companies may seek software to manage thousands of endpoints. Others may wish to add threat hunting tools.
Whether you're a solo entrepreneur or a company with its own security operations center (SOC), the best endpoint security software can meet your needs and safeguard your IT systems. Check out the list below to find a solution that best meets your business security needs.
| Product | Description | Next Steps |
|---|---|---|
|
Kaspersky Endpoint Security
Rating image, 4.00 out of 5 stars.
4.00/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
Kaspersky Endpoint Security delivers simple yet effective endpoint protection for small businesses. Check out this review for details.
|
|
|
Bitdefender GravityZone Business Security
Rating image, 4.00 out of 5 stars.
4.00/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
Check out this comprehensive review for Bitdefender GravityZone Business Security to see if it’s the right endpoint protection solution for your company.
|
|
|
Microsoft Defender Antivirus
Rating image, 4.00 out of 5 stars.
4.00/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
Microsoft Defender Antivirus is free on computers running Windows. Check out this review to learn if it’s enough for your business.
|
|
|
Avast Business Antivirus Pro
Rating image, 4.00 out of 5 stars.
4.00/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
Avast Business Antivirus Pro combines all the components of a strong antivirus and security suite with some awesome tools to secure the SMB environment.
|
|
|
McAfee Endpoint Protection
Rating image, 3.90 out of 5 stars.
3.90/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
Read this review to learn if McAfee Endpoint Protection makes sense for your company’s endpoint security.
|
|
|
Sophos Intercept X
Rating image, 3.80 out of 5 stars.
3.80/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
Discover the pros and cons of Sophos Intercept X in this comprehensive review. Learn if it’s the right endpoint security software for your business.
|
|
|
ESET Endpoint Antivirus
Rating image, 3.70 out of 5 stars.
3.70/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
ESET Endpoint Antivirus offers strong malware prevention capabilities. Read this in-depth review to understand its pros and cons.
|
|
|
VMware Carbon Black
Rating image, 3.70 out of 5 stars.
3.70/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
Read this review of the VMware Carbon Black Cloud Endpoint Standard product to learn if it’s the right endpoint security software for your business.
|
|
|
CrowdStrike Falcon
Rating image, 3.60 out of 5 stars.
3.60/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
Check out this detailed CrowdStrike Falcon review to discover if it’s the right endpoint security software for your business.
|
|
|
Symantec Endpoint Protection
Rating image, 3.50 out of 5 stars.
3.50/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
Check out this in-depth Symantec Endpoint Protection review to see if it’s the right endpoint security software for your business.
|
|
|
Webroot Business Endpoint Protection
Rating image, 3.50 out of 5 stars.
3.50/5
Our ratings are based on a 5 star scale.
5 stars equals Best.
4 stars equals Excellent.
3 stars equals Good.
2 stars equals Fair.
1 star equals Poor.
We want your money to work harder for you. Which is why our ratings are biased toward offers that deliver versatility while cutting out-of-pocket costs.
|
The Webroot Business Endpoint Protection platform is built for small businesses. Check out this review to learn if it’s the right software for your company.
|

Small businesses will find effective, easy-to-manage malware protection through Kaspersky Endpoint Security. Built for companies with a small IT team and fewer than 100 employees, Kaspersky Endpoint Security provides a preconfigured protection platform, called Kaspersky Endpoint Security Cloud, made for quick deployment and simple ongoing security oversight.
Kaspersky’s defenses stopped all malware and zero-day attacks used in independent tests while accurately identifying legitimate software, avoiding false positives. Its technology works without impact to computer performance, even on older machines.
The platform provides protection for Windows, Mac, and mobile endpoints. IT teams oversee these endpoints through a web-based console. This console offers features to manage various security aspects, including device encryption, scanning of removable drives, and a firewall.

The Cloud Discovery widget provides insights into staff use of external services. Image source: Author
Kaspersky designed its solution for quick, easy deployment. The console guides your IT team through the steps to configure and enable Kaspersky Endpoint Security Cloud.
Once you’re set up, many options exist to fine-tune your IT security. Set automated scans to occur when computer usage is at a minimum to reduce performance impacts to users. Manage the types and frequency of security email notifications. Set the aggressiveness of security scans to determine the intensity of protection you desire.
The platform includes reports and a dashboard furnishing security insights. You can identify where endpoint vulnerabilities exist, and discover the types of threats the platform has stopped. The Monitoring dashboard includes a Cloud Discovery feature that lets you analyze how your staff are using external cloud services such as Google Drive.
Pricing starts at $405 per year for 10 endpoints. Discounts are available for new customers, multi-year purchases, and for purchases involving more endpoints.

Bitdefender GravityZone Business Security is a powerful IT security solution designed for small businesses. GravityZone protects over 500 million endpoints worldwide, performing 11 billion queries per day, and leveraging machine learning to analyze this massive data trove to evolve protection methods.
It stops cyberattacks using multiple layers of protection. This approach combines machine learning, heuristics, event correlation, browser-based security, endpoint risk analytics, continuous monitoring of computer processes, and more to block malware and other threats.
Bitdefender’s proprietary technology constantly assesses software application processes for signs of malicious behavior. It can catch zero-day attacks targeting network vulnerabilities. It scans incoming web traffic in real time -- even on secure connections -- to prevent malware downloads, and it automatically blocks phishing and fraudulent web pages.
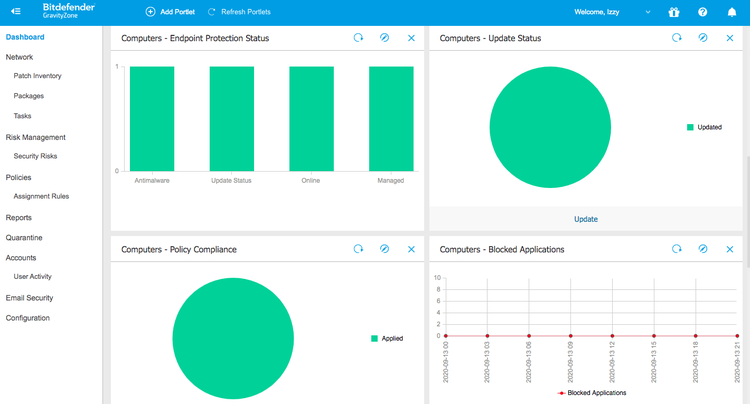
GravityZone’s customizable dashboard provides a view into key areas of your IT security. Image source: Author
When threats are detected, GravityZone takes action. It quarantines infected files, stops suspicious processes, and rolls back any changes performed by an attack.
You can manage IT security in a single interface housing protection policies, user accounts, risk analytics, and reporting. GravityZone provides insights to identify and address your IT network’s vulnerabilities.
From installation to ongoing management, GravityZone makes IT security oversight simple and quick. Even companies with small IT teams can obtain enterprise-level protection by using GravityZone’s comprehensive tools.
If you need technical help, Bitdefender has your back. The company offers 24-hour phone support along with an extensive online knowledge center, as well as email and chat support options.
Bitdefender allows you to test drive GravityZone with a free 30-day trial. Simply sign up for an account to begin the trial -- no credit card required.

Technology icon Microsoft, known for its Windows operating system, is equally known for a history of subpar antivirus protection. Its previous Windows Defender product generally performed poorly in independent tests.
Microsoft has worked to turn that around. In 2020, the tech giant released a rebranded antivirus solution, replacing the old Windows Defender product with the superior Microsoft Defender Antivirus. The new solution’s malware protection capabilities are potent.
Independent testing firm AV-Test Institute subjected Microsoft Defender Antivirus to over 13,000 malware samples. Microsoft’s product successfully stopped them all. Against hundreds of zero-day threats, which exploit undiscovered software vulnerabilities, it again stopped 100%, better than the industry average of 98.9%.
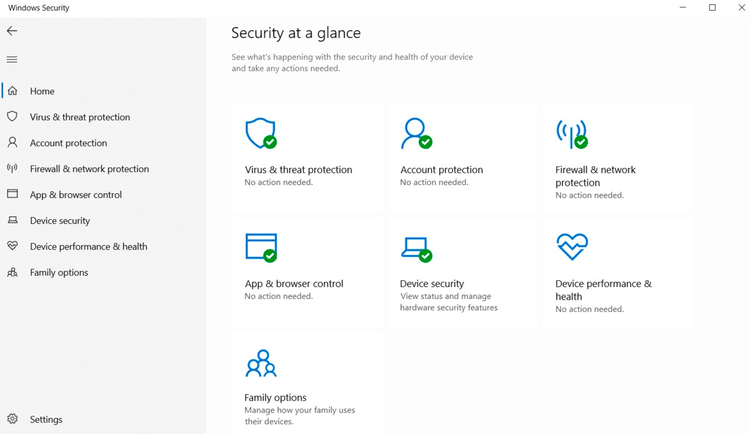
Microsoft Defender Antivirus acts as the threat protection option in Windows Security. Image source: Author
What makes Microsoft Defender Antivirus superior to its predecessors? The new solution adopted technologies such as machine learning, data analysis, and Microsoft’s cloud computing infrastructure. This allows Microsoft Defender Antivirus to identify hidden threats and attacks trying to circumvent traditional detection methodologies.
Microsoft Defender Antivirus does its job well, but offers no other endpoint protection features. It stops at stopping malware.
It’s part of the Microsoft Windows Security suite, which offers a few other protection capabilities, such as a firewall. But if you require tools to manage multiple endpoints, set security policies, and other IT tasks, neither Microsoft Defender Antivirus nor Microsoft Windows Security is going to fill those functions.
That said, Microsoft Defender Antivirus comes with two big advantages. It’s pre-installed as part of Microsoft Windows Security on all Windows machines, saving your IT team the trouble of setting up and deploying the software. It’s also free.
That value is hard to pass up, especially for small businesses with limited budgets and even smaller IT departments. This makes Microsoft Defender Antivirus a viable option for organizations with little or no IT team.


One of the biggest and oldest cybersecurity firms, McAfee is a storied brand in the IT industry. The company offers a wide range of security products for companies of all sizes, and its McAfee Endpoint Protection system includes small business protection through its McAfee Endpoint Security platform.
This platform’s threat-prevention capabilities proved flawless at stopping malware and zero-day threats in test scenarios. McAfee Endpoint Security also made no mistakes differentiating legitimate software from cyberattacks. Its only flaw was a slight impact on computer performance around application installation and when launching apps.
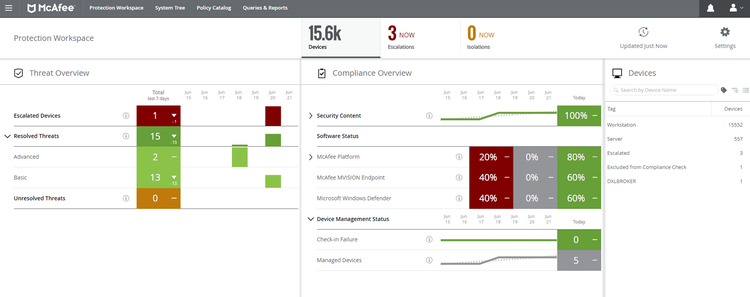
The McAfee ePO console delivers a variety of security insights. Image source: Author
McAfee Endpoint Security includes key protections, such as a firewall and the ability to block users from browsing infected websites. One of the platform’s distinguishing features is its Adaptive Threat Protection (ATP).
ATP allows McAfee Endpoint Security to recognize all types of malware, including sophisticated threats such as fileless attacks. It uses the McAfee Global Threat Intelligence network, reputation parameters, and your risk criteria to evaluate suspicious activity and decide on remediation actions.
McAfee helps IT teams oversee your company’s security through its McAfee ePolicy Orchestrator (ePO). ePO serves as a central management console with the ability to set security policies, view and analyze endpoint status, take action when threats are detected, and assess the overall health of your company’s security.
Because McAfee offers many security solutions, such as encryption capabilities, XDR (Extended Detection and Response), and managed services, it can meet the needs of any security scenario. These include regulatory requirements for your industry.
McAfee pricing starts at $31.06 per year for each license for its McAfee Endpoint Protection Essential for SMB. You can test-drive its McAfee Endpoint Security platform and ePO tool with a free trial.

For businesses seeking a comprehensive IT security solution, Sophos Intercept X fits the bill. It protects endpoints from malware, ransomware, browser-based attacks, and many other cyber threats.
Sophos Intercept X employs an artificial intelligence approach called deep learning to identify attacks, including those that have never been seen before. Anti-ransomware abilities complement deep learning, rolling back unauthorized attempts to encrypt files for ransom.
For attacks that circumvent security, Sophos Intercept X offers endpoint detection and response (EDR) to hunt them down. Tools identify potentially infected endpoints and map out the entire attack chain. It also outlines recommended next steps, streamlining the threat hunting process.
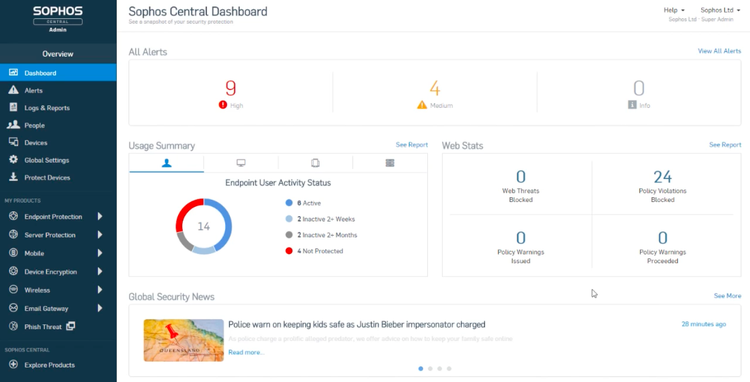
Sophos Intercept X’s wide capabilities are managed through a single console. Image source: Author
Administer Sophos Intercept X’s extensive features through a single interface called Sophos Central. You can configure and manage all your Sophos products through this web-based portal. Sophos Central lets you efficiently set up your IT network users, security policies, and other protection elements.
Sophos Central surfaces security alerts and analysis through its dashboards and reports. Options include a list of blocked threats, unprotected endpoints, and users who tried to access blocked websites or download dangerous software.
Its features are so vast, Sophos Intercept X can address the needs of any size organization. Whether you have a few endpoints or thousands, Sophos Intercept X provides the tools to manage endpoint security. Mobile devices, laptops, servers, virtual machines, wireless equipment, and cloud-based infrastructure are all supported.
Sophos Intercept X is only available through third-party vendors. These partners provide a range of prices depending on your security needs. If you only need to protect a few endpoints, you can expect to pay in the $54-68 range per user for an annual subscription. The cost can start at $28 per user if you’re protecting hundreds. Sophos furnishes a list of partners in your area.

ESET Endpoint Antivirus provides potent malware protection for small businesses. Independent testing verified the software’s effectiveness at stopping malware and zero-day attacks. Its proprietary protection technology combines artificial intelligence, behavioral evaluations, and reputation and data analytics to accurately detect and prevent cyberthreats from infiltrating your IT network.
The software is for small businesses with up to 250 endpoints, such as laptops and servers. ESET Endpoint Antivirus offers cloud-hosted and on-premises options, although the former lacks protection for mobile devices and virtual environments.
Your IT department manages ESET Endpoint Antivirus capabilities through a single web console, the ESET Cloud Administrator. It is convenient to set security policies for your endpoints, manage users, and create and track security tasks through this console. You can quickly obtain insights into your security posture from the platform’s robust dashboard and reporting capabilities.
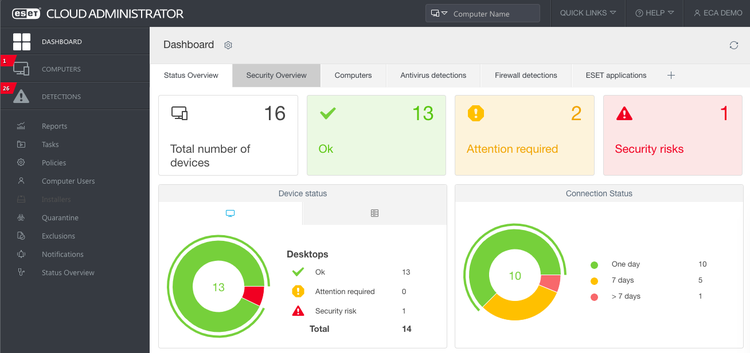
The ESET Endpoint Antivirus dashboard is packed with useful insights. Image source: Author
Your ESET Endpoint Antivirus implementation starts you off with default security settings to get you up and running right away. It also offers various options to deploy its software agent to your endpoints, allowing you to choose the method that makes the most sense for your IT team.
ESET Endpoint Antivirus encompasses ESET’s foundational endpoint protection technologies. Bundles featuring additional ESET security products are available, such as its ESET Endpoint Security package, which includes the same antivirus protection along with a firewall.
The price for ESET Endpoint Antivirus depends on several factors: the number of endpoints you’re protecting, whether you’re opting for the cloud-hosted or on-premises solution, and the number of years you’re subscribing to the product. A year of on-premises coverage is $190 for five endpoints. The same five endpoints cost $239/year for the cloud-based solution.

VMware Carbon Black Cloud Endpoint Standard is Carbon Black’s foundational endpoint security product for businesses. It’s intended for larger companies with a dedicated IT team seeking more advanced protection beyond mere antivirus software.
Carbon Black’s product combines next-generation antivirus (NGAV) capabilities with endpoint detection and response (EDR) to sniff out threats that traditional antivirus software can’t detect. It’s packed with deep data insights and security options.
These features allow an IT team to dig into every security event with the information needed for quick investigation. With this info in hand, IT teams can use VMware Carbon Black Cloud Endpoint Standard to take action, such as quarantining an infected computer or whitelisting a developer’s new programming script.
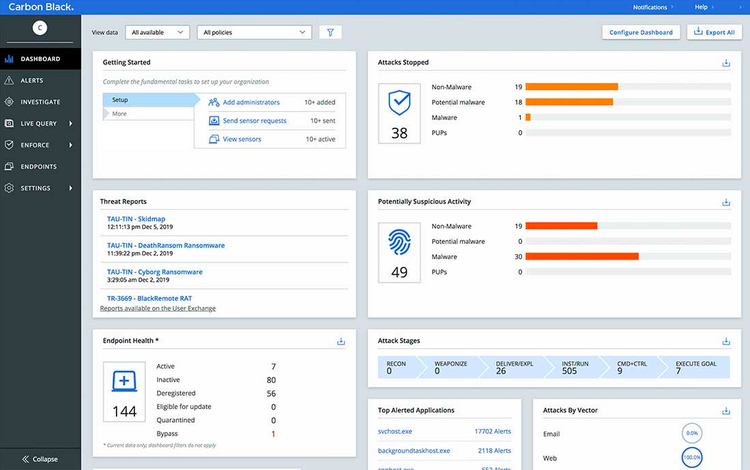
The Carbon Black dashboard serves as your security hub. Image source: Author
VMware Carbon Black Cloud Endpoint Standard comes with an intuitive security management console. Staff can view the overall health of your IT network, and dissect threats based on factors such as its attack chain lifecycle stage, and attack vectors including email and websites.
Carbon Black protection proved effective against most malware in independent tests. It didn’t perform as well as industry averages against zero-day exploits, and it slowed computer performance more than rival solutions.
These detractions are offset by the platform’s wealth of security data, including a visual, interactive breakdown of attack chains that isn’t often included in the introductory solutions of other security software. This allows IT teams to dissect and address attacks quickly.
VMware products, including VMware Carbon Black Cloud Endpoint Standard, are purchased through third-party vendors. Pricing varies across these partners and depends on the number of endpoints protected and years of service you’re subscribing to. VMware provides a list of partners on its website.

The CrowdStrike Falcon platform is one of the newer endpoint security solutions on the market. Its deep integration of threat intelligence is one of its distinguishing features, providing companies with a security operations center (SOC) and the details necessary to catch cybersecurity threats.
CrowdStrike Falcon is easy to implement, even alongside other protections. Its security agent is lightweight, ensuring minimal impact on endpoints and end users.
CrowdStrike offers a modular design to its product suite, enabling businesses to easily add the components that meet their needs. CrowdStrike Falcon encompasses a wide range of security options from a firewall to threat-hunting services.
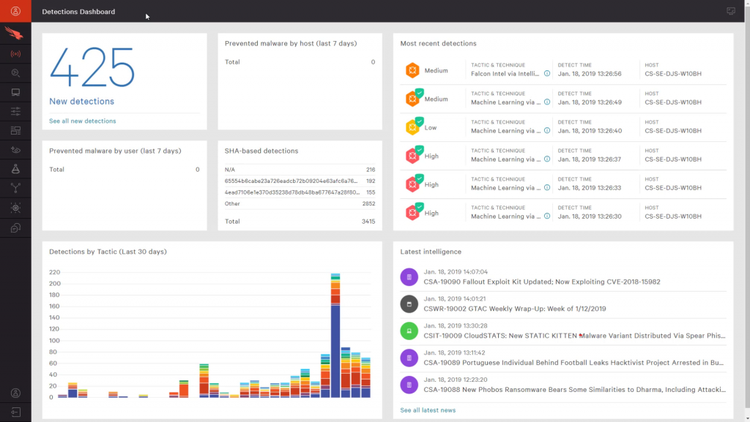
The Falcon dashboard highlights key security threat information. Image source: Author
Its platform comes with next-generation antivirus. This technology improves on traditional antivirus software by leveraging a combination of artificial intelligence, malware behavioral analysis, and threat intelligence to identify and stop cyberattacks, even from never-before-seen malware.
CrowdStrike Falcon is a cloud-native platform, built from the ground up to operate in the cloud. This gives it infinite scalability, eliminates the need for separate hardware and maintenance, and prevents attackers from gaining access to the security technology.
The platform’s management console makes it efficient to manage thousands of endpoints. The console provides security policy configuration, and its search and filter capabilities allow you to quickly drill down to the data or endpoint group you’re looking for.
CrowdStrike Falcon pricing starts at $8.99/month for each endpoint. On an annual basis, CrowdStrike’s cost is higher than rivals, so you’ll have to assess if the price makes sense for your business. To that end, CrowdStrike provides a 15-day free trial to test-drive its platform.

Small businesses with a dedicated IT team will find compelling security capabilities in Broadcom’s Symantec Endpoint Protection (SEP) software. It combines artificial intelligence (AI) with proprietary features to protect endpoints, such as laptops and servers, from a range of cyber threats including malware and zero-day exploits.
SEP collects and collates cybersecurity data from millions of systems around the globe to evaluate the safety of every file accessed online. Its AI analyzes billions of factors, such as the origin point of the file, to correlate data between users, files, and websites in determining if a file is safe. The AI also examines trillions of known good and bad files in Symantec’s global intelligence network to block previously unknown malware before the attack executes.
Symantec Endpoint Protection employs a single software agent and user interface, the SEP Manager, to deploy and manage its security features. It also comes with preconfigured security settings, such as default policies. These elements make it easy to get SEP up and running quickly.
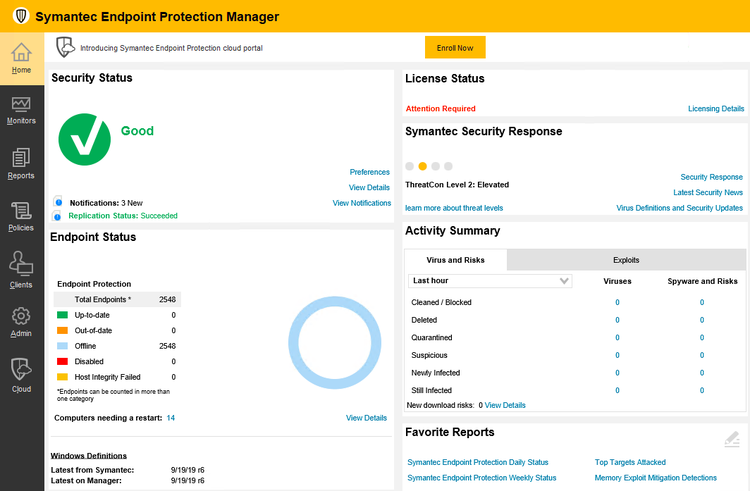
A single interface makes Symantec Endpoint Protection functionality easy to manage. Image source: Author
The SEP Manager console is intuitive and easy to navigate. Yet its depth of configuration capabilities and SEP’s proprietary protection features presents a learning curve to gain understanding of all your options.
SEP covers the security basics around attack prevention. These include reports to analyze the health of your IT security, policies to define how you want to handle endpoints, and administrative features to manage your domains and servers.
You purchase Symantec Endpoint Protection through third-party vendors. These partners provide a range of annual subscription prices depending on the number of endpoints you’re looking to protect. Broadcom provides a list of partners on its website.

Small businesses with limited IT staff will find Webroot Business Endpoint Protection a compelling offering. It’s easy to set up and use, providing protection for your business without a big time investment.
Simply download and install Webroot’s lightweight software agent onto endpoints, which takes just seconds. From there, you oversee endpoint security through a web-based management console. Because the agent doesn’t conflict with existing security software, you can have Webroot’s platform up and running quickly.
Webroot uses machine learning technology in its cloud infrastructure to constantly monitor endpoints without slowing down computer performance or requiring complex installations. Webroot’s proprietary technology continues to provide protection even when endpoints are offline.

SecureAnywhere’s customizable dashboard delivers insights into your IT security. Image source: Author
Webroot is preconfigured to get your IT security up and running quickly, efficiently, and with minimum effort. Since all security happens through the cloud, endpoint protection occurs with minimal human oversight.
Webroot’s platform also handles threat remediation automatically. It quarantines threats, and its patented technology preserves the data and system changes on your endpoints. If an infection occurs, this technology allows you to restore endpoints to an uninfected state without having to completely wipe your computer and start over.
Webroot Business Endpoint Protection covers the IT security basics. Create whitelists and blacklists to manage website access and the software processes allowed to run on your network. Create endpoint security policies or use the preconfigured ones. Run reports to analyze vulnerable areas and assess the health of your IT network.
Pricing depends on the number of endpoints you want to protect. Annual subscriptions cost $30 per endpoint with a five-endpoint minimum. A free trial lets you test-drive Webroot to ensure it meets the unique needs of your organization.
What The Ascent looks for in great endpoint security software
Business antivirus protection is a core component of every endpoint security product. It's the key capability required to deliver malware defense.
Beyond that, it's important to consider features such as server antivirus and other factors impacting a company's security. While every business will prioritize some elements over others, the following are common needs for every organization.
Threat protection
Protection is the most important characteristic of endpoint security software. You buy this product to defend your organization against cyberthreats. If it can't do that well, other features don't matter.
But threat protection isn't simply a matter of offering enterprise antivirus. It must go beyond traditional antivirus solutions. Today's sophisticated types of malware can easily circumvent traditional antivirus products.
These top endpoint security software products all use several technologies to proactively combat cybercriminals and their constantly evolving tactics. Machine learning and behavioral analysis are among the methods proven to work well against today's cyberthreats. The availability of more advanced security solutions, such as endpoint detection and response (EDR), add to the value of many security vendors on this list.
Remediation capabilities are also important. It's impossible to stop all attacks all the time. Some will eventually slip through. When that happens, your endpoint security solution must effectively address these incidents, such as automatically reverting back files encrypted by ransomware.
Ease of use
Great endpoint security software should be easy to use. IT teams have a lot on their plate, and they don't have time to figure out complex software or suffer through many manual steps to complete a task that should take a couple of mouse clicks.
Easy-to-use security software is particularly important. A wrong setting or configuration can leave your systems exposed to cyberattacks.
Modern endpoint solutions, such as the ones on this list, are about streamlining the security experience. Initial setup usually entails installation of the software's security agent onto endpoints, and you're done. Many platforms come with preconfigured policy settings, allowing IT teams to get their security in place within minutes.
Daily maintenance is simple as well. The security platform sends alerts for discovered threats while remediating issues in real time. Your IT team only needs to log into the platform's dashboard to scan your security posture, address any concerns, such as patching out-of-date software on endpoints, and move on with their day.
Robust support
When you run into trouble with your endpoint security software, the longer it takes to resolve, the more your business is exposed to cyberattack. You need fast resolution. That's why robust support options are an important factor when evaluating endpoint security products.
Many on this list provide 24-hour phone support, a reassuring recourse when emergencies arise. All offer an online self-service portal to find product manuals, how-to documents, training videos, and other self-help material.
Some offer community forums to gain insights from fellow users, and share news about the latest security threats. If you're stuck with a non-emergency issue, chat help is another option.
How your business can benefit from using endpoint security software
The right endpoint protection software increases your IT team's efficiency and productivity when overseeing company security, without sacrificing safety. Beyond that, endpoint security solutions deliver several important benefits affecting your company's ability to grow and expand. Let's look at a few key ways it helps.
Protect sensitive data
Endpoint security software's primary benefit is to protect your company's most important data. Whether that's customer records, financial information, proprietary technology, or even digital photos of the kids on your work laptop, endpoint security stops criminals from achieving their objectives.
Usually these criminals try to encrypt your files, then demand a ransom if you want those files restored. They may also stay hidden in your IT systems, silently collecting your company data to sell to other criminals, perform identity theft, or other illegal activity. Today's cybercriminals are sophisticated, making the task of stopping them a challenge.
The best endpoint security software meets this challenge by leveraging technologies that identify threats, even those lurking in your systems posing as legitimate processes. If you don't have reliable endpoint security software, or worse, none at all, you're allowing criminals free rein to do what they please with your IT systems and business data.
Preserve customer trust
Protecting your customers' data is essential to business success. If your company suffers a security breach, customers lose confidence that their data is safe with you.
At that point, you'll lose customers, and will need to provide an incentive or perform goodwill outreach to rebuild that trust. This not only costs you money, it may still not help retain all your clients.
With endpoint security software, you avoid this scenario altogether. The software blocks attacks before getting to your customer data, and even if an attack slips through, the endpoint security protection minimizes or even reverses the damage done.
Prevent financial losses
Cyberattacks lead to tangible financial losses. The average cost to organizations affected by a cyberattack is $200,000 in damages. For some small businesses, that would mean their demise.
The most common malware attack is ransomware. The cybercriminal encrypts your data and extorts you for significant sums of money. On top of that, you'll incur costs to rebuild trust with customers.
Endpoint security software addresses these issues. Not only are common attacks blocked if ransomware manages to slip in and encrypt important files, some endpoint security solutions can reverse the encryption, restoring your files without paying a penny to the criminal.
Another benefit is regulatory compliance. If your IT systems don't comply with legal or industry regulations, you could be fined or blocked from doing business. The endpoint security vendors on this list can help you meet any regulatory requirements.
Our Small Business Expert
We're firm believers in the Golden Rule, which is why editorial opinions are ours alone and have not been previously reviewed, approved, or endorsed by included advertisers. The Ascent does not cover all offers on the market. Editorial content from The Ascent is separate from The Motley Fool editorial content and is created by a different analyst team.










