Business security used to be simple: Lock up everything valuable at the end of the day. Now it's a 24/7 proposition because every enterprise network and its applications, hardware, and endpoints are vulnerable to security intrusions.
In smaller companies, the information technology (IT) department oversees network security. As your business grows, though, your data security needs may increase until you require a dedicated security operations center (SOC).
We'll go over SOC basics, benefits, and the steps to setting one up so you can decide if a SOC solution is right for your business.
Overview: What is a security operations center (SOC)?
The SOC is a specialized IT department that monitors, detects, investigates, and responds to multiple types of cyber threats to protect enterprise networks, hardware, software, websites, and endpoints from security intrusions.
The SOC continually scans the network for threats, weaknesses, and deficiencies to mitigate before they turn into critical issues or incidents.
SOC cyber security operations incorporate tools and processes such as security information and event management systems (SIEMs), breach and instruction detection, firewalls, and probes.
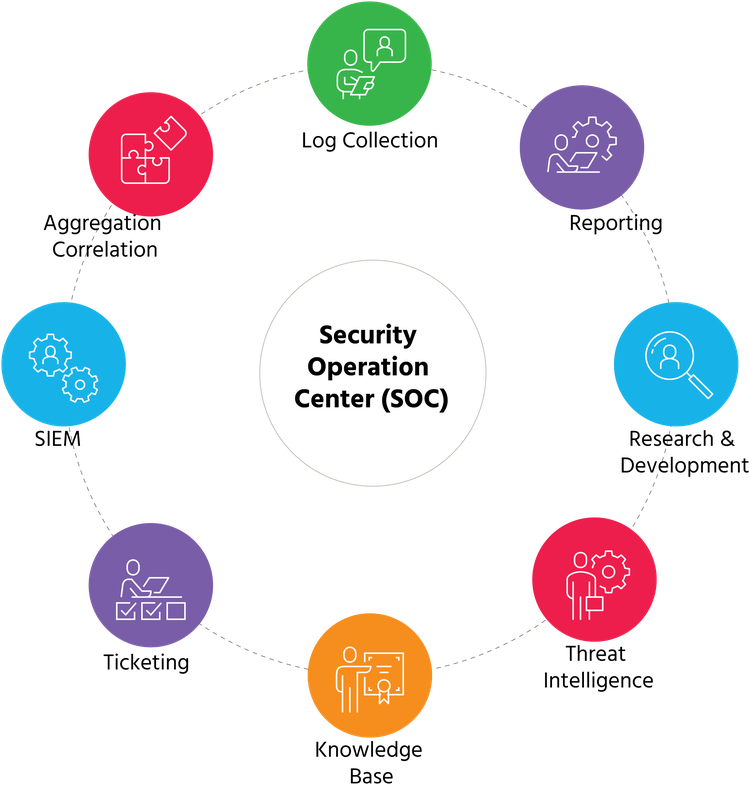
SOCs use multiple processes and tools to reduce or negate security threats. Image source: Author
SOC monitoring and investigation activities focus on daily operational security and are less concerned with designing or developing security strategies and architecture. Information Technology Infrastructure Library (ITIL) problem management protocols also help support SOC activities.
Companies that don’t want the expense of setting up their own SOC can use a third-party security operations center as a service (SOCaaS) provider.
SOC vs. NOC: What's the difference?
The SOC is similar to the network operations center (NOC), but they do have key differences.
While the SOC's mission is to protect enterprise networks, systems, and data from security threats, the NOC is responsible for overall network availability, maintenance, and performance related to service-level agreements (SLAs) and user service requests.
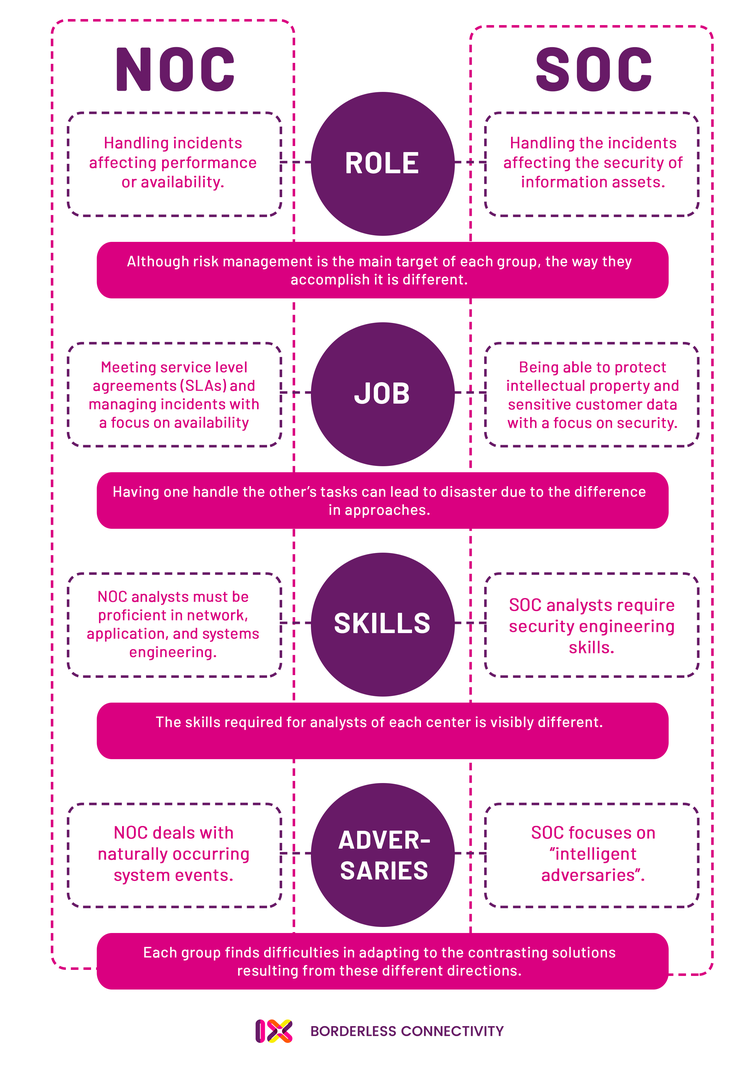
SOCs and NOCs help manage enterprise IT systems, each with different responsibilities and objectives. Image source: Author
Approximately 80% of organizations with a SOC also have a NOC. Due to their overlapping functions to ensure IT system integrity -- call centers, incident response teams, and network monitoring -- one option to increase efficiency is to merge them into an integrated operations center (IOC).
Benefits of creating a security operations center
Every business with an enterprise network and related assets needs IT risk management. The SOC enhances this effort with its dedicated team to identify, prevent, and mitigate security threats. Beyond increased security, a SOC creates additional benefits.
1. Reduced costs
The financial benefits due to less downtime can be dramatic: 80% of small businesses have experienced downtime with costs ranging from $82,200 to $256,000 per event. The SOC further lowers expenses because a unified security team results in less overlap in job duties.
The SOC also helps you avoid fines and other penalties due to violations of the Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), and other data security regulations.
2. Centralized activities
IT security functions are often spread between different workgroups and locations, but the SOC brings them together in a single team. This improved collaboration leverages their shared knowledge and experience to optimize results.
The SOC also serves as a single point of contact to coordinate security activities and disseminate key information and policies.
3. Increased prestige
Customers and employees demand their information remain secure once they give it to you. A SOC demonstrates to stakeholders you are serious about data protection. Don't keep your SOC a secret: Make it an integral part of your internal and external marketing materials.
How to set up a security operations center (SOC)
The SOC setup process is complex and requires a significant initial investment, so make sure you're ready for this undertaking. Follow the steps below to create a SOC with the right mix of people, procedures, and technology.
Step 1: Identify your objectives and capabilities
Focus your SOC project and control costs with careful upfront planning that addresses these two elements:
- Business objectives: Security for the sake of security is not the SOC's mission. Use ITIL processes to align SOC activities with defined business objectives and the critical systems and data that support those goals.
- Current capabilities: A SOC typically combines existing personnel, processes, and assets, so perform a comprehensive audit to identify and leverage current capabilities to reduce costs and avoid redundancies.
Creep is the enemy of every project and setting up a SOC is resource intensive, so identifying your desired outcomes and current assets will contribute to an effective project plan.
Step 2: Design the SOC
Identify an initial set of business-critical use cases to define the SOC's scope.
These essential SOC definitions include:
- Functional requirements: Identify performance requirements and sources of log, event, and threat intelligence data.
- SOC operations: Determine hours of operation, total personnel, and positions.
- Technical architecture: Choose a SIEM platform, existing applications to integrate, workflows, and automation processes.
SOCs can perform a wide range of high-level processes, but focus first on core functionality -- monitoring, detection, incident management, and recovery -- to simplify the setup process. Once those are implemented and running well, think about adding additional features such as vulnerability management.
Step 3: Assemble the SOC team
The SOC's strength comes from its narrow focus on security threats. While you may have current staff who can perform some SOC duties, invest in outside talent when necessary to create the best team.
Essential SOC personnel include:
- SOC manager: Supervises the SOC team and reports to the chief information security officer (CISO)
- Security analyst: Provides real-time risk management and security intelligence
- SIEM engineer: Oversees SIEM administration, incident response, and vendor management
- Forensic investigator: Analyzes incident data, evidence, and behavior analytics
- Incident responder: Conducts initial investigations and threat assessments using incident response plans (IRPs)
- Compliance auditor: Ensures SOC procedures remain in compliance with government regulations and industry standards
A co-managed SOC, which combines internal employees with independent contractors, can reduce personnel overhead.
Step 4: Equip the SOC
The SOC requires specialized applications besides SIEM and IT management software.
These software tools include:
- Cyber threat intelligence databases and feeds
- Governance, risk, and compliance (GRC) systems
- Firewalls, including next-generation firewalls (NGFW)
- Intrusion detection systems (IDS)
- Intrusion prevention systems (IPS)
- Penetration testing tools
- Vulnerability scanners
- Wireless intrusion prevention
It’s not wise to cut budget corners when equipping the SOC. Your team requires a robust set of tools to achieve the multiple benefits a SOC can generate.
Step 5: Measure SOC performance
SOC metrics for overall performance and individual team members are essential to achieve maximum efficiency and effectiveness.
Common SOC metrics include:
- Events over time
- Outages by minute
- Percentage of escalated incidents
- Time to containment and eradication
- Percentage of recurring incidents
- Rules generating false positives
These metrics also help identify technology or skill gaps to address.
Advance your security efforts now
Securing company data and customer information is critical for every business. When you're ready to take that protection to the next level, a SOC provides 24/7 security for your enterprise network and related assets.
Our Small Business Expert
We're firm believers in the Golden Rule, which is why editorial opinions are ours alone and have not been previously reviewed, approved, or endorsed by included advertisers. The Ascent, a Motley Fool service, does not cover all offers on the market. The Ascent has a dedicated team of editors and analysts focused on personal finance, and they follow the same set of publishing standards and editorial integrity while maintaining professional separation from the analysts and editors on other Motley Fool brands.