We all have secrets no one needs to know. I consider myself a red-blooded native Texan, but I'm also a not-so-proud yet enthusiastic devotee of "Married at First Sight: Australia," and, for reasons I still don't quite understand, cried like a baby after watching Richard Linklater's "Boyhood."
While I don't normally volunteer this information, if other people know it -- or somehow figure it out -- the flow of happiness in my life will remain uninterrupted.
The same thing is not true when it comes to my passwords. I have more than 50 password-protected devices and applications -- everything from my iPhone and Chromebook laptop to my mortgage, checking, email, and credit card accounts. If any of those are compromised, the end is nigh.
The stakes are even higher at your small business. Every digital device (aka "endpoint”) connected to your computer network is a potential entry point for bad actors to access confidential information.
Strong passwords are your first and best step toward endpoint security. We'll go over the features of effective passwords and the best practices to create them so you can better protect your small business.
Overview: What makes a strong password?
A strong password has two characteristics: It's easy to remember but hard to guess.
The harder part is getting people to do both these things. Instead, because nobody is prepared when a request for yet another new password appears, we rely on the same bad password ideas.
These include using easily guessed passwords such as qwerty or 12345678, reusing passwords, or adding a number to the end of an old password to update it.
The stakes are too high for businesses to use weak passwords:
- Data breaches compromised 4.1 billion records in the first half of 2019.
- A data breach's average cost was $3.92 million in 2019.
- Security breaches have increased 67% since 2014 and 11% since 2018.
Even worse, 43% of data breaches occurred at small businesses with an average cost of $150 per stolen record. Poor password management policies undermine the strongest passwords.

Strong password management policies are essential to protect your company's data. Image source: Author
Hackers use multiple tactics to crack passwords:
- Brute force: An automated program generates password combinations using every possible character string until it produces your password.
- Dictionaries: Another automated program uses a dictionary to combine words and abbreviations in common ways such as aceofspades or iloveu.
- Public information: Personal information -- such as birthdays, favorite sports teams, or a pet's name -- are found online and often used in passwords.
- Existing data breaches: Information is acquired from previous hacks sold online, which highlights the danger of reused passwords.
- Phishing: Fraudulent messages are sent via email, text, phone, or social media channels asking for login credentials.
These multiple attack methods highlight the importance of strong passwords and identity management strategies.
6 tips for creating a strong password
Creating passwords is not difficult, but it does require some careful thought to protect your business's data. Follow the password suggestions below to create and maintain the best passwords possible.
1. Password best practices
The first step in creating strong passwords is to avoid obvious choices by using these password tips:
- Longer is better: A brute force attack requires progressively more time the longer your password is. Eight characters is the minimum length to use, and 15 or more is better.
- Never reuse passwords: If you reuse passwords, hackers will have access to multiple accounts when they figure out one password.
- Don't add numbers to passwords: When asked to update a password, many users add the next number in sequence -- 2 or two and so on -- to the end of it. Hackers know this and account for it in brute force or dictionary attacks.
- Avoid obvious character substitutes: Using "$" for "s" may feel pretty slick, but hackers also know this and incorporate common substitutions into their algorithms to discover password variations such as @ceofsp@des.
- Don't use personal information: Your favorite movie? Sports team? Birthday? This information is publicly available in multiple places online, starting with your social media accounts, so don't use it in your passwords.
The blessing and curse of these tips is, while they help you avoid easily discovered passwords, you're left with a pressing question: How are you supposed to create a strong password you can also remember?
2. Passphrases
Instead of creating your password from a common word or phrase, use a passphrase that employs a combination of unrelated words or characters:
- Word strings: Pick a sequence of words based on visual, not semantic, cues. For example, if I look left to right at my desk, I see a fan, monitor, and lamp, which I can combine into a 14-character string: fanmonitorlamp. I can further shake things up with character substitutions and capitalizations such as F@nMonitorL@mp, which are more effective because the words are not part of a common phrase.
- First letters: Another method is to use the first letter of each word from a phrase you use. For example, I'm prone to saying, "Beer is proof that God loves us and wants us to be happy." Taking the first letter of each word produces a 13-character string: biptgluawutbh. Again, using character substitutions or capitalizations makes this password even harder to discover.
Passphrases work well because they're easy to recall and will thwart most dictionary and brute force attacks.
3. Test passwords
If you're unsure how strong a potential password is, or are unconvinced different strategies affect its strength, test your passwords. One popular password strength detector rates each of the following passwords based on how long it would take to crack them:
- qwerty: instantly
- aceofspades: one day
- @ceofsp@des: five months
- fanmonitorlamp: 51 years
- F@nMonitorL@mp: 29 million years
- giptgluanutbh: 1 year
- BiptGlu@wutbh: 400,000 years
I doubt anyone can guarantee a password is secure for 29 million years; however, the different timeframes here illustrate relative password strength.
4. Password managers
A password manager application creates a secure digital repository for encrypted login information for multiple applications, devices, and websites. If you have a network security operations center, a password manager is an essential component.
The best password managers also include features to create passwords and ensure you don't reuse the same password. An online random password generator may appear attractive as a free alternative, but a third-party password generator could have its own security issues you have no control over.
5. Multi-factor authentication (MFA)
Increase the strength of your passwords with multi-factor authentication (MFA). This security system requires a second piece of information that only you have to complete the login process.
Different authentication factors include:
- Answers to personalized security questions
- Codes generated by smartphone apps
- Codes sent via email or text
- Facial recognition
- Fingerprints
A typical MFA example is when I log into my bank account. After I submit my password from my laptop, the bank texts a single-use code to my smartphone that I must also enter before accessing my account.
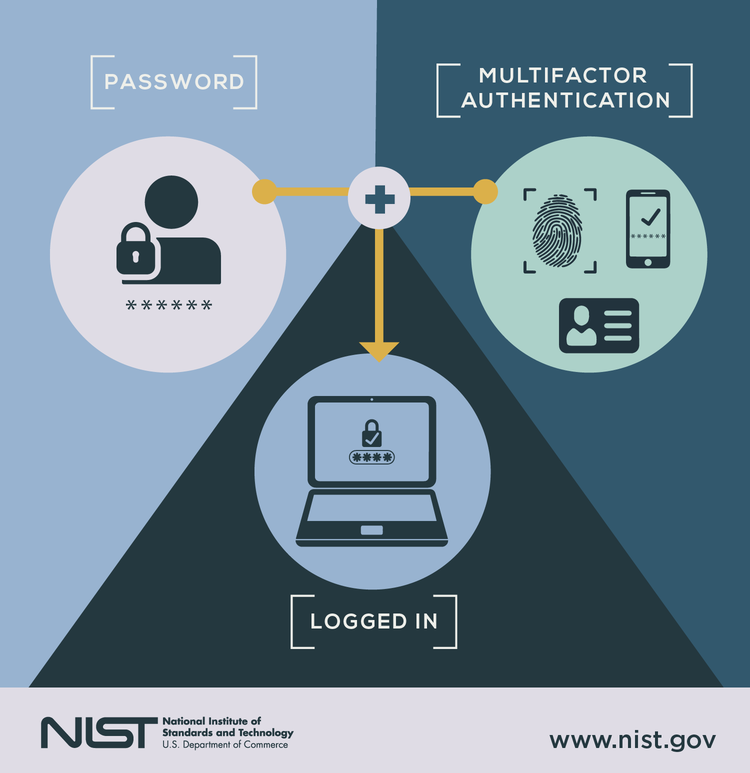
Multi-factor authentication provides an extra layer of device and network security. Image source: Author
MFA with adaptive authentication uses artificial intelligence (AI) to flag atypical logins and adjust security enforcement policies based on risk level. If a user logs in from a new location or device, for example, adaptive authentication deploys extra authentication factors before providing account access.
6. Check passwords
The strongest password in the world isn't effective if it's already compromised. A variety of different websites, browser extensions, and applications can provide information about potential password hacks:
You probably have enough already going on in your head without giving your collection of passwords much thought, but a password report like the one below from Google should be a wake-up call.

This is not the Google Password Checkup report you want. Image source: Author
Passwords are like hot water heaters. Both should work when needed, but you'd like to give them little thought beyond that other than infrequent maintenance. The key things, however, are doing the proper setup and periodic upkeep.
Strong passwords are your security starting point
If you don't want to leave your network's protection up to your employees and the passwords they choose, use the best endpoint security software. These applications use a multifaceted approach to secure company data so you can protect confidential information and avoid the costs of a data breach.
Our Small Business Expert
We're firm believers in the Golden Rule, which is why editorial opinions are ours alone and have not been previously reviewed, approved, or endorsed by included advertisers. The Ascent does not cover all offers on the market. Editorial content from The Ascent is separate from The Motley Fool editorial content and is created by a different analyst team.