In a cryptojacking attack, the victim is tricked into running cryptocurrency-mining computer code on behalf of the attacker. It may sound harmless, but cryptojacking incidents can cause serious problems.

What is cryptojacking?
What is cryptojacking?
Cryptojacking is a sneaky attack. The attacker isn’t grabbing personal data or financial service logins from their victim, and the intrusion will not lock down your computer like in a ransomware attack. Instead, your computer system ends up running code that generates cryptocurrency on behalf of the intruder.
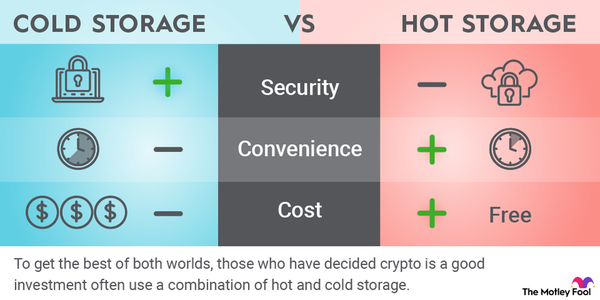
Blockchain Wallet
Cryptojacking explained
Cryptojacking explained
A cryptojacking attack can take many forms, but the end goal is always the same. The attacker wants to make your computer or smartphone run malicious code that generates cryptocurrency tokens without your knowledge.
The tokens are associated with cryptocurrency wallets under the intruder’s control, so the victim’s hardware essentially puts money directly into the hacker’s pocket.
The cryptojacking malware becomes a burden on the host computer, consuming resources such as memory and processor cycles. The malware may also serve as a foot in the door for more dangerous attacks, putting the victim’s private, corporate, and financial data at risk.
How cryptojacking works
How cryptojacking works
The attack begins by placing malicious code on the target system. This critical step may involve download strategies, code injection tactics, or a mix of the two.
In a download attack, the victim downloads and executes the malicious code. The code can be included in seemingly legitimate download material such as program files or digital videos, or a link to the malware may be included in a genuine-looking email. Either way, a single click is usually all it takes to download the bad code and run the cryptojacking code.
Injection attacks are different because the victim’s computer never downloads code to run as a separate process. Instead, the malware is included as a JavaScript module in websites or online ads. The JavaScript code runs while the ad or website is displayed in a web browser.
Some cryptojacking modules may spread through a combination of injection and download attacks, increasing the attack’s reach and the potential for larger cryptocurrency payouts.
Most cryptojackers use privacy-focused cryptocurrencies such as Monero (XMR 0.79%) or Zcash (ZEC 0.9%). It is possible to mine other cryptocurrencies in a cryptojacking attack, but this particular type of digital coin makes it difficult to track down the owner of any particular token. When combined with a proof-of-work cryptocurrency architecture such as Zcash and Monero, where new tokens can be mined by common computers, you get an effective combination for cryptojackers who want to maximize their crypto-mining results without risking their identity.
Once the code is running on your computer (or phone, or tablet, or any other computing device), you may notice that other tasks are slowing down as the cryptojacking program consumes your available resources. If your system has a task manager available, you may find that one process is using up every available processor cycle and lots of memory. This is the cryptojacking program or the web browser the cryptojacking injection script is using.
Cryptojacking examples
Cryptojacking examples
A cryptojacking injection tool known as Coinhive was found on more than 4,000 websites in February 2018. The sites had installed a screen-reading accessibility tool called BrowseAloud, and one version of the software had been altered by hackers to include the Monero-mining malware.
The popular plugin affected visitors to popular sites such as the U.S. courts system, several city government hubs across the U.K. and Ireland, and the British Information Commissioner’s Office. The hacked software was active for about 13 hours before BrowseAloud maker Texthelp shut the screen reading service down and fixed the code.
Some security experts called this the biggest cryptojacking attack ever, but the swift response limited the actual damage. A post-mortem analysis of the event found that the hackers earned less than $30. At the same time, some saw the event as a test run for future cryptojacking injection attacks on a large scale.
Four years later, cybersecurity firm AlienVault found a Monero-mining installer file that sent the mined tokens to a university in North Korea. This file may have spread through email-based phishing attacks, by tapping into security flaws in a popular web server platform, and the usual collection of malware-spreading vectors.
The target of the crypto-mining software’s Monero transactions was inactive when AlienVault found it. The security experts noted that the North Korean connection might be a prank, or the software might have been an experiment run by students at the university. As a result, this particular installation file probably didn’t generate much money for the people behind it, but the North Korean angle generated plenty of headlines at the time.
Some cryptojacking efforts are more profitable. The WatchDog cryptojacking operation started in January 2019 and had generated more than $32,000 in Monero tokens when it was uncovered by network security specialist Palo Alto Networks (PANW -1.71%) in 2021. In this instance, the Monero tokens were generated by a software package downloaded to commercial-grade cloud computing instances.
How to prevent cryptojacking
How to prevent cryptojacking
Good cybersecurity practices are the best defense against cryptojacking. Here’s the drill:
- Install and run both anti-malware scanners and virus protection software where you can.
- To minimize your exposure to injection attacks, you can disable JavaScript and install ad-blocking software in your web browsers. There are downsides to this strategy since some sites won’t work properly without JavaScript and ads.
- Don’t click on emailed links unless you know that the source can be trusted -- and even then, make sure that the link points to a safe target address.
- Keep an eye on your system’s processor and memory usage and dive in for a deeper look if some process is consuming more resources than expected.
Cryptojacking hackers and security experts are always fighting to outsmart each other. The defenses that worked yesterday may be targets for a new workaround tomorrow, so it’s important to keep your anti-malware tools up to date.