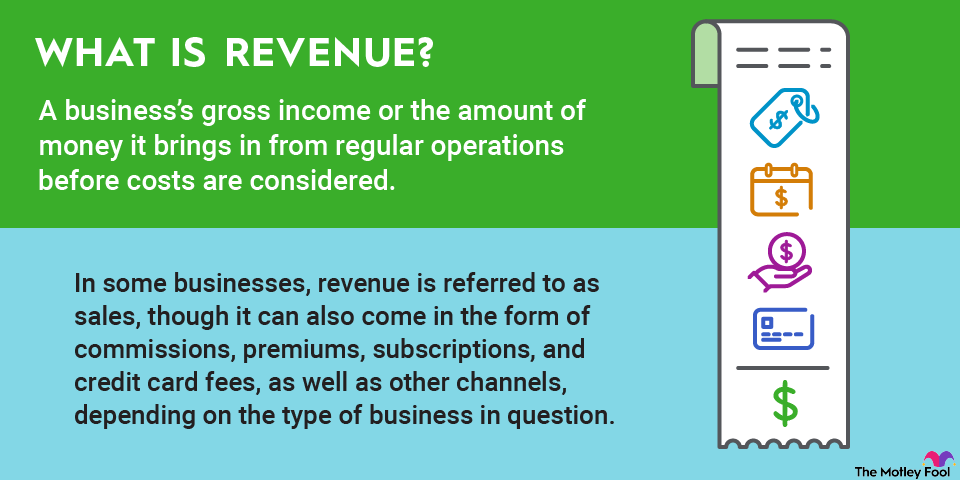
Risk management is the process of identifying, evaluating, and controlling legal, financial, and physical threats. Although the concept can be applied in many situations, it's often discussed in relation to business and investing.
Let's explore principles and techniques of risk management so you can apply them to protect your wealth and well-being.

Understanding risk management
Risk management is a proactive approach to mitigating or diffusing threats. The multistep process is versatile enough to address almost any threatened subject, including yourself, your finances, your business, and your portfolio. These are the steps:
Step 1: Identify potential threats
Formal business risk assessments are often expansive. Areas of focus can include technology systems, security protocols, the competitive landscape, projected workforce needs relative to the available labor pool, sustainability practices, expected capital needs, and more. Any of these topics could reveal potential threats to ongoing business operations.
Capital
Risk identification can also be more targeted. If you were attempting to mitigate a known risk, such as getting laid off, you might look for contributing threats related to your job function, seniority, and expertise. The health of your industry and the potential for your company to win new business may also be factors.
Step 2: Evaluate threats
In the evaluation phase, you estimate the likelihood of each identified threat's occurrence and the potential outcome. You can then prioritize threats and, if applicable, allocate resources to manage them or determine next steps.
A business risk assessment, for example, might reveal cybersecurity threats that could damage the company's reputation and invite expensive lawsuits. The justification of resources to address the issue would likely hinge on the probability of getting hacked.
Regarding your assessment related to job security, you might conclude that your highest-priority threat is the nonessential nature of your job. In the next step, you'll decide how to protect yourself from this threat.
Step 3: Devise and implement control measures
Once high-priority threats are identified and evaluated, you can strategize on remediation steps. The business might hire a cybersecurity consultant to shore up its systems, for example. You might ask your manager for added responsibilities that make you more valuable to your employer.
Step 4: Monitor threats
Threats can evolve in their probability of occurring and in their consequences. Monitoring is necessary for early detection of threats that may be increasing in severity.
Investment risk can also be managed more broadly. Many investors will employ some combination of risk avoidance and risk reduction with these basic strategies:
- Establish an investing approach to guide decision-making. Your investing parameters will determine which risks you accept and avoid.
- Diversify. Combining assets that respond differently to economic and market conditions can lessen volatility. This is because some assets will rise when others fall, which limits extreme value swings.
- Maintain long holding periods. The market grows more consistently over longer periods than shorter ones. While the major market indexes have had many single-year losses, there has never been a value loss over 20 years or more.
- Invest funds you can afford to lose. Investing excess funds rather than essential funds allows for longer holding periods.
Everyday risk management
You are likely practicing risk management informally on a regular basis. How fast you drive, your discretionary spending habits, and how you interact with coworkers are habits commonly influenced by some level of risk aversion. More obviously, you probably hold one or more insurance policies that transfer the risk of financial loss to your carrier.
Related investing topics
While you may not need to evaluate your risk of getting a speeding ticket, there are benefits to applying risk management techniques to your insurance purchases. Identifying and evaluating potential threats to your car or home relative to your coverage, for example, will either reveal a savings opportunity or contribute to your peace of mind. The possible outcomes are:
- You're carrying too much insurance. You can safely trim your coverage and save on premiums.
- You're carrying the right amount of insurance. You can keep your coverage the same but continue monitoring your risk going forward.
- You're not carrying enough insurance. Carrying too little car, home, or life insurance coverage could wipe you or your family out financially. You could accept this risk and do nothing or raise your limits to feel more secure in your financial position.
In short, risk management tactics may have roots in business, but they're versatile enough to apply to financial and personal matters. Use them to navigate uncertainties, protect your wealth, and improve peace of mind.